Author: Richard Curteis - Director
Published: 04/05/2025
M&A Due Diligence: De-Risking Deals in the Age of Exploits & Stolen Credentials
Realize Security's services align to today's threat models to provide fast and accurate results which address compliance requirements and provide actionable intelligence to address risk. Our clients can expect completion in days, or even hours, rather than in weeks. Compounded with Realize Security's competitive rates, this means, fast, accurate and cost-effective compliance-focussed outputs and investment-committee reports when you need them.
Cybersecurity due diligence (DD) in Private Equity (PE) buyouts is a critical value-protection exercise. Ignoring weaknesses in a target company can lead to significant post-acquisition costs, operational disruption, and reputational damage. Mandiant (Google Cloud) recently released their M-Trends 2025 Report, providing clear data showing where attackers are focusing. For PE firms, understanding these vectors is key to understanding the modern threat landscape and leveraging that understanding to reduce risk to investment.
This year's report highlighted two dominant attack vectors that should be top-of-mind during mergers and acquisitions (M&A) due diligence: exploitation of externally exposed vulnerabilities and the use of stolen credentials. In this post we unpack what Mandiant found and why it matters.
TL;DR
Mandiant's 2025 report confirmed attackers overwhelmingly favoured exploiting perimeter weaknesses (33% of breaches) and using stolen credentials (16%, and rising). These are major risks for M&A, potentially hiding significant liabilities. Traditional checklist DD isn't enough; you need rapid technical validation focused on these vectors. Our approach delivers exactly that, through a time and cost-effective solution.
Mandiant M-Trends 2025: The Attacker's Playbook
Mandiant's frontline incident response data painted a clear picture: attackers follow the path of least resistance, often targeting the digital front door.
1. Exploits Still Reign Supreme (33% Initial Access):
- For the fifth year running, exploiting vulnerabilities was the most common way attackers breached organisations globally.
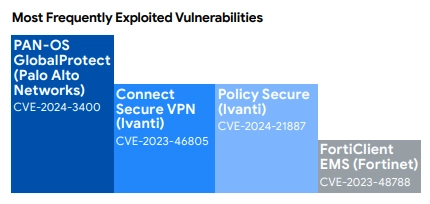
- Focus Area: Edge devices (VPNs, firewalls like Palo Alto Networks, Ivanti, Fortinet) were prime targets. Mandiant highlighted specific CVEs (like ,CVE-2024-3400, CVE-2023-46805 and CVE-2024-21887) that were heavily exploited, often as zero-days initially.
- M&A Impact: An unpatched perimeter device or externally facing application in your target company is an open invitation. This represents immediate risk and potential urgent remediation costs post-close. Identifying these before the deal is signed is crucial.

Source: Mandiant M-Trends 2025 Report
2. The Rising Tide of Stolen Credentials (16% Initial Access, Up from 10%):
- Stolen credentials overtook phishing as the second most common initial infection vector.
- The Engine: Infostealer malware (like VIDAR, RACCOON, REDLINE) vacuuming up credentials from employee or contractor systems (even personal devices used for work) fueled this trend. These stolen credentials ended up on dark web markets. Mandiant's report detailed the UNC5537/Snowflake incident , where credentials stolen years prior via infostealers led to major data theft.
- M&A Impact: This vector is insidious. A target company might look secure from a traditional scanning perspective, but compromised employee or third-party credentials can provide attackers easy access, bypassing many defences. This risk often lies hidden, requiring more than just infrastructure scanning to uncover. Brute-force attacks (often against RDP or VPNs with weak/default credentials) were also highlighted, especially for ransomware intrusions (26% of vectors).
3. Cloud Isn't Immune and Credentials are the Key:
- Attackers are adapting to cloud environments. Mandiant found stolen credentials were a primary vector for cloud compromises (35% of cases studied).
- Social engineering to reset MFA (as seen with UNC3944) or using credentials stolen via infostealers (UNC5537) provided direct access to cloud resources.
- M&A Impact: Assuming a target's cloud environment is inherently secure due to the provider's infrastructure is dangerous. Identity security, credential hygiene, and proper configuration are paramount and must be validated during DD.
Source: Mandiant M-Trends 2025 Report
The M&A Due Diligence Imperative: Beyond the Checklist
These findings underscored why deep technical cyber due diligence is critical for PE firms:
- Hidden Liabilities: Exploitable vulnerabilities and compromised credentials represent significant, often hidden, liabilities that can materialise post-acquisition.
- Remediation Costs: Fixing these issues can be expensive and time-consuming, impacting your investment thesis.
- Operational & Reputational Risk: A breach shortly after acquisition can severely damage the portfolio company's operations and reputation.
- Regulatory Scrutiny: Breaches involving sensitive data trigger regulatory investigations and potential fines.
Traditional, slow-paced penetration testing during an already tight M&A timeline might not provide the rapid, focused insights needed on these specific, high-impact vectors. Waiting weeks for a report detailing vulnerabilities found through time-consuming scans, potentially missing the critical credential exposure element, isn't ideal.
Our Approach: Faster, Focused Cyber DD for M&A
We've aligned our external security assessment approach specifically to address today's threat models and the needs of PE due diligence, focusing on efficiency and actionable intelligence, and not billing for idle scan time.
How we tackle the key risks:
Rapid External Attack Surface Analysis:
- We use intelligent automation to quickly discover and assess the target's internet-facing assets. Servers, web apps, APIs, VPNs, remote access and administration services.
- This quickly identifies the exploitable vulnerabilities and misconfigurations attackers leverage.
Credential Exposure Monitoring:
- We integrate checks for compromised credentials associated with the target company available in data breaches - directly addressing the problem of stolen credentials.
Focus on Analyst Validation & Reporting:
- Automation handles the heavy lifting of discovery, scanning and initial triage.
- Our expert analysts focus on validating findings, assessing real-world risk in the M&A context, and producing clear, actionable reports.
What this means for your PE Due Diligence:
✅ Speed: Get critical insights within the M&A timeline, not weeks later, potentially, in hours.
✅ Focus: Prioritise the highest-risk vectors. External vulnerabilities and credential exposure.
✅ Cost-Effective: Pay for expert analysis and reporting, not automated scan time.
✅ Actionable Intelligence: Understand the real cyber risk exposure and potential remediation needs before you close the deal.
✅ CREST Accredited: Assurance of quality and alignment with supplier compliance requirements.
✅ Compliance: ISO 9001 and ISO 27001 accredited service.
Secure Your Investment: Integrate Modern Cyber Due Diligence
The Mandiant M-Trends 2025 report confirmed that attackers are successfully exploiting basic weaknesses in perimeter security and identity management. For PE firms, overlooking these during M&A due diligence is a gamble.
Our streamlined, threat-focused approach gives you the technical insights needed to evaluate cyber risk accurately and efficiently, helping you to de-risk investment and protect value.
Ready to enhance your M&A cyber due diligence? Get in touch to learn how our rapid, focused assessments can safeguard your next acquisition.
Our Mission
To deliver expert application penetration testing with AI-powered analysis at transparent, flat-rate pricing, enabling organisations to secure their web, API and mobile applications without compromise.